This project is about a Telegram bot with the ability to execute terminal commands from your Telegram account and with the command response as messages.

Initially, I started this project for personal needs, but I decided to release it because of the sure need of many with the same problem. I encountered and based in a project of Va5c0 .
It often happens in a pentest or even more a bug bounty, that you need to enumerate targets or processes that take a lot of time as certain types of nmap scans, cracking some hash. And many times for that reason I leave that process working, checking if it is finished or not, leaving the computer on, sometimes with nothing else to do, sometimes I had to leave and turn off the computer leaving all the previous process without results. It is a high cost of time and money.
So now I share this little project of a bot (which I baptized as Bot Bounty) that can be used by a single person or several, as a company with this same need to improve productivity. Either on a computer, VPS, or a Raspberry. Keeping the degree of security that no one but the people who are authorized to use the bot will use it (in case someone external comes across the bot and try to use it).
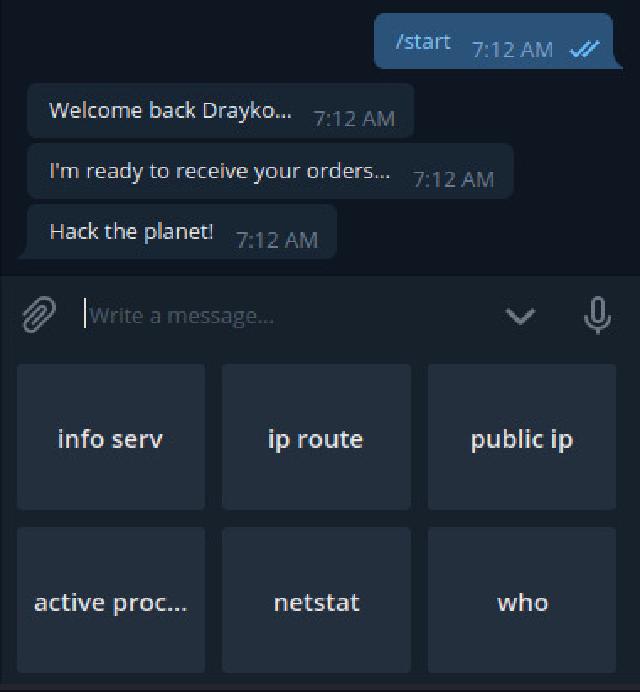
The bot has predefined options for quick access to information that can be useful for bot usage. To mention a few: the available RAM space (info serv/RAM option), or the public IP of the device on which the bot is running.
In addition, with the command /exec you can execute any command that is available in our terminal of the device to use, for example:
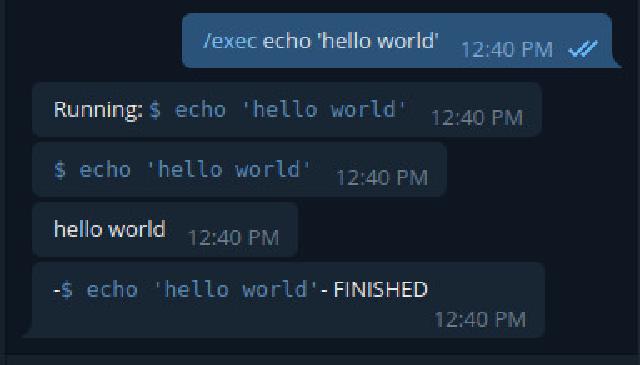
Thus limiting itself to commands that require interaction, such as some unforced installation with the typical -y or logging in via SSH, to name a few examples.
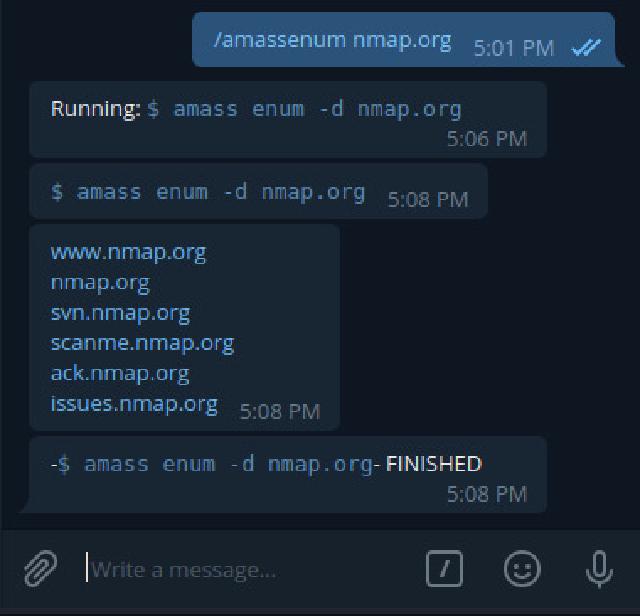
For example, in amass, the command is /amassenum, which calls $ amass enum -d to perform an enumeration of subdomains:
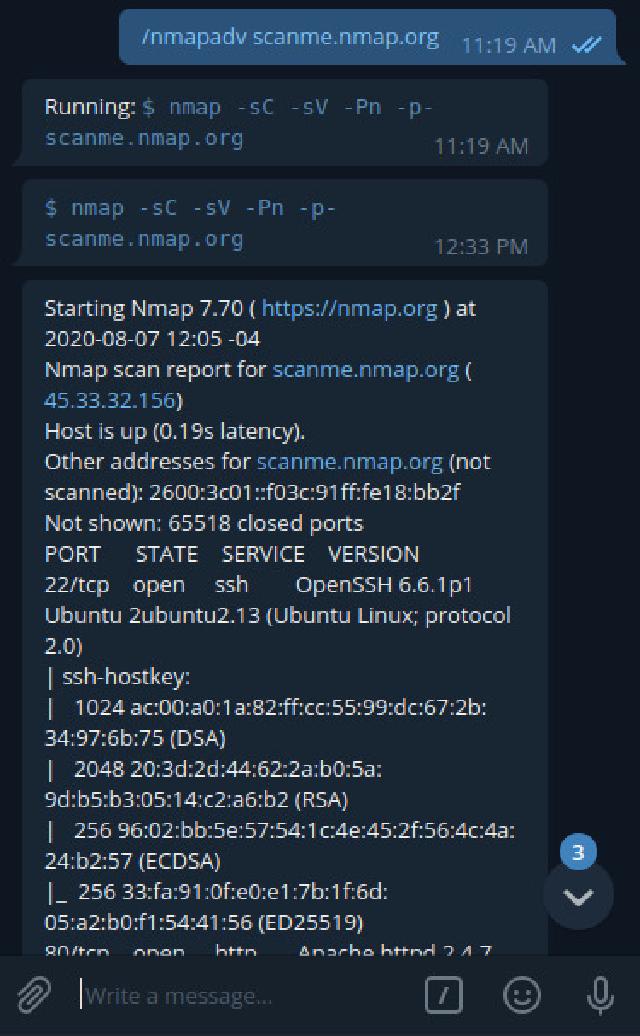
In nmap we have a scan with the scripts, by default, pull out the port versions found, avoid performing host discovery (check if it is alive), and search all possible ports; i.e.: $ nmap -sC -sV -Pn -p-.
Of course, to use these commands, the tools must be installed in the system you are using to run the bot (and you can call them directly in the console).
As a first release, we only have these commands; however, I am waiting for other shortcut commands to add to the bot that you suggest. Also, if you find bugs, you can write to me or issue an issue in the repository.
The repository is as follows: Bot Bounty
Pre-configurations
To use it previously you must create a bot in Telegram and replace the API KEY that gives by the value specified in the script at line 12.
TOKEN = 'XXXXXX:XXXXXXXXXXXXXXXXXXXXXXXX'.
In addition to register the user ID(s) that will use the bot, in line 14:
authorizedUsers = [123456789, 987654321]
And now just run the script.
$ python3 bot.py
Tips
**If the command’s output is too big, you should save it in a file and without output **.
for example:
nmapadv example.com > resultsExample.txtnmapadv example.com -oN resultsExample.txtexec echo 'awesome bot!' > yesItIs.txt
To check for possible unauthorized users trying to use the bot, a log of all executed commands with user details is kept in the file logFileBot.txt.
And that would be it, for now; I hope this work is well received.
-Hackers are People Too 😜
