Hey there!
This is the first post in a series covering CTF challenges held during the International Congress on Information Security (CIDSI), organized by the Agency for Electronic Government and Information and Communication Technologies (AGETIC), thanks to the efforts of the Cyber Incident Management Center (CGII). The event took place from November 29 to December 1, 2018.
We’ll start with the demo CTF challenge organized by CGII.
1. Submit the flag
This is a simple challenge meant to demonstrate how the platform works.
All you need to do is submit the flag. The flag is: 327a6c4304ad5938eaf0efb6cc3e53dc
Solution: The challenge literally gives you the flag:
327a6c4304ad5938eaf0efb6cc3e53dc
2. Website
Now it gets slightly more “difficult.” A developer from AGETIC left a hint on the event’s website. Link: https://www.cgii.gob.bo/eventos/cidsi2018/
Solution: Inspect the page’s source code using F12 or Ctrl+U.
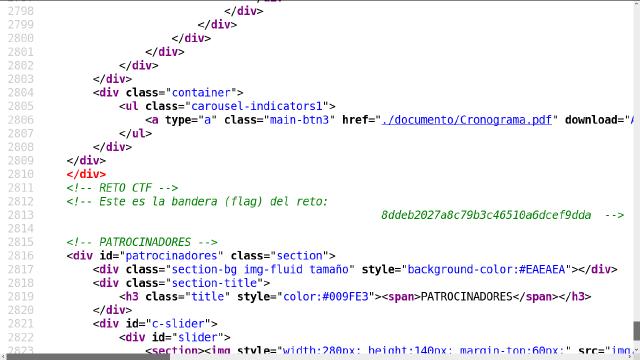
And there it is:
8ddeb2027a8c79b3c46510a6dcef9dda
3. Admin Panel
Poor security configurations.
Developers often use default or easy-to-guess passwords.
You’re starting to explore your hacking skills and while visiting a company, you connect to their internal network. Surprise! You find the admin panel for their employee system. Your mission: log in as admin and get the flag.
Solution: There are many common/default credentials (check this list ).
Let’s try the classic: admin/admin
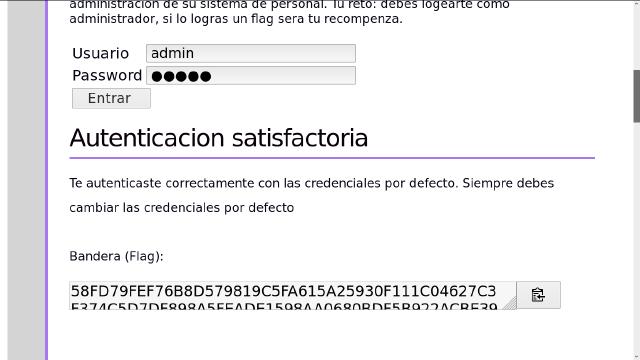
Nice! Here’s the flag:
58FD79FEF76B8D579819C5FA615A25930F111C04627C3F374C5D7DF898A5FEADE1598AA0680BDF5B922ACBE396691FD1943A181E362F32FFCC0B29A6DD725BA0
4. Cracking
Cracking the hash
MD5 is no longer considered secure.
A hacker friend doing a security assessment got access to a user database. If he can break a hash and log in, he’ll gain more privileges. Help him crack this outdated hash:
3cc31cd246149aec68079241e71e98f6
Solution: Google the hash — luckily, it’s been indexed. Tools like Hashcat or John The Ripper could help too.
Pa$$w0rd
5. Cracking 2
You’re chilling in a five-star hotel. A friend captures network traffic with Wireshark and happens to sniff a login to a staff portal with hotel promotions. The password looks “encrypted” — but you’ve got this. The hash:
ODcwMzM2NzA5ODUwMDUzNA==
Solution: Looks like Base64. Tools to detect encodings are easy to find online.
The flag is:
8703367098500534
6. Cracking 3
While capturing traffic, you find what looks like a hash:
MNQXA4TJMNXXE3TJN4======Mission: decode it.
Hint: It’s “half as hard” as Base64.
Solution: The hint points to Base32. The flag is:
capricornio
7. Cracking 4
A friend missed their first crypto class in a security postgrad course and needs help decoding this:
ynivqnrftravnyHint: If today were “Tuesday the 13th,” things would be easier.
Solution: This is a reference to ROT13 . Use any ROT13 decoder.
The flag:
lavidaesgenial
8. Find user
Developers often forget to sanitize user input.
We found a site that offers VIP invites to exclusive events. To access them, you need to trigger a JavaScript alert. Can you do it? If you’re the dev pro we think you are, the flag will be your reward.
Solution: This suggests a basic XSS . Try something like:
<script>alert("XSS")</script>
And voilà!
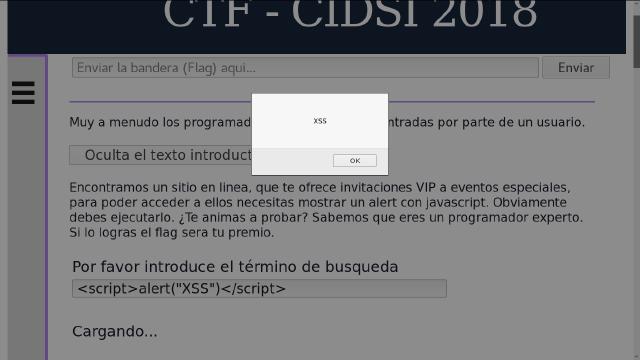
Followed by:
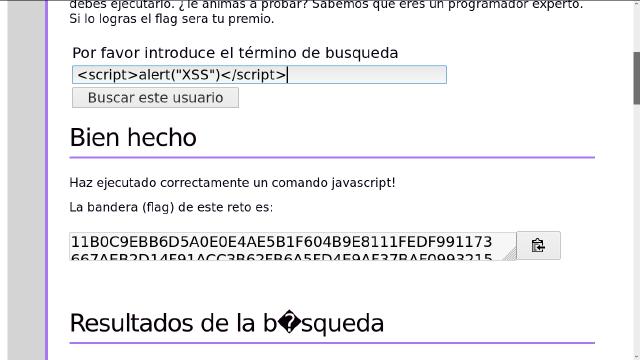
The flag:
11B0C9EBB6D5A0E0E4AE5B1F604B9E8111FEDF991173667AEB2D14F91ACC3B62FB6A5FD4E9AF37BAF09932150BF0D89A3B89F2B9F135347799D95DB38A4AC515
9. View profile
Progressing nicely! A chocolate company is giving away chocolates to random users. To see the list, you need admin rights. Currently, you’re just a tech user. Your mission: gain access to the admin profile. Your reward? Chocolate — and the flag, which is the admin’s contact info.
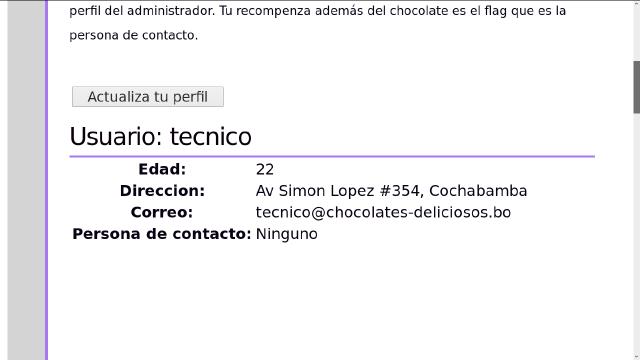
Solution: Check the request headers when clicking “Update profile”:
POST /eventos/cidsi2018/ctfdemo/lessons/fdb94122d0f032821019c7edf09dc62ea21e25ca619ed9107bcc50e4a8dbc100 HTTP/1.1
Host: www.cgii.gob.bo
Content-Type: application/x-www-form-urlencoded
username=tecnico
Change the username to:
username=administrador
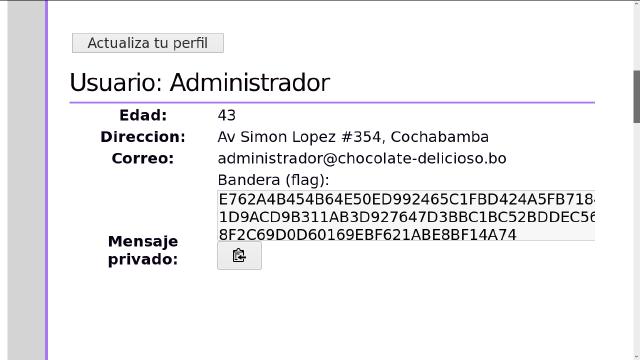
And there’s your flag:
E762A4B454B64E50ED992465C1FBD424A5FB7184E9AA89B901D9ACD9B311AB3D927647D3BBC1BC52BDDEC560A005F72638F2C69D0D60169EBF621ABE8BF14A74
As we’d say in Bolivia… esito sería. More write-ups will be published and linked soon. Stay tuned!
Hackers are People Too 😜
Series links

